Dolit httpftp kernel demo
Author: a | 2025-04-24
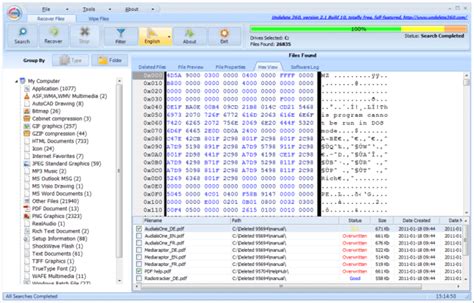
Download Dolit HttpFtp kernel demo latest version for Windows free to try. Dolit HttpFtp kernel demo latest update: Aug Download Dolit HttpFtp kernel demo latest version for Windows free to try. Dolit HttpFtp kernel demo latest update: Aug.
Dolit HttpFtp kernel demo - CNET Download
The driver, runPTEditorLoader.exe --unloadAlternatively, you can also use any other driver-loading tool, e.g., OSRLoader or NoVirusThanks Kernel-Mode Driver Loader.Install Kernel Part From SourceLinuxBuilding the kernel module requires the kernel headers of the kernel. On Ubuntu, they can be installed by runningsudo apt install linux-headers-$(uname -r)Both the library and the the kernel module can be build by runningThe resulting kernel module can be loaded usingsudo insmod module/pteditor.koWindowsThe kernel driver for Windows requires Visual Studio with Visual C++, the Windows SDK, and the Windows Driver Kit (WDK) to build.Using the Visual Studio project, the driver can then simply be built from Visual Studio.RequirementsThe library requires a recent Linux kernel (continuously tested on the current kernel for Ubuntu 16.04 (kernel 4.15), 18.04 (kernel 5.3), and 20.04 (kernel 5.8)) or Windows 10.It supports both x86_64 and ARMv8.The library does not rely on any other library. It uses only standard C functionality.On Linux, the library does not require root privileges, whereas on Windows it requires administrator privileges.TestTo test whether the kernel part and the library works, the repository contains unit tests.The tests are found in the folder test and can be compiled with make (Linux) or Visual Studio (Windows).ExampleThe basic functionality (ptedit_init and ptedit_cleanup) is always required.After the initialization, all functions provided by the library can be used.For examples see example.c or the examples in the demo folder.The demo folder contains multiple examples:memmap: Starting from the root of paging, the demo iterates through all page tables of all levels and dumps the contents of the entries.map_pt: A Rowhamer exploit simulation, which maps the page table to a user-accessible address for manipulation.uncachable: This demos manipulates the memory type of a mapping to uncachable and back to cachable.nx: After setting a function to non-executable, it uses the page tables to make the function executable again.virt2phys: Converts a Nucleus Data Recovery Kernel for Word Recovery recovers corrupted word document files corrupted due to unexpected system shutdown, virus attacks or error reading media where word document are stored. The software uses Live Preview technology. After complete scanning the corrupted or damaged word document which are recoverable are shown in the preview window, then recovered data is copied at the user defined location. Multiple doc files are repaired in a single repair cycle. Kernel for Word Document Repair Software uses quick algorithm for searching and repairing the corruptions in the corrupted document files and hence is a fast, simple and easy to use Word Document Repair Software, which helps you to recover and repair your corrupt document files in minutes. Kernel for Word recovery software’s supported versions includes MS Word 2010, 2007, 2003, 2000, 97, 95 and 6.0 documents. Free demo version of the software is available for easy download. Demo version recovers and saves recovered data to new Word file at the defined location. However, the file repaired using demo version will have stamp Demo after every paragraph. User Rating: 1.5 (2 votes) Currently 1.50/512345 OS: Win2000, Windows 7 x32, Windows 7 x64, WinServer, Windows Vista, Windows Vista x64, Windows XP Requirements: Pentium II 400 MHz, 64 MB RAM, 10 MBDolit HttpFtp kernel demo for Windows - CNET Download
With RankingExample "Your query found 349,871 possibly relevant documents. Here are the first eight." Examination of the first 8 finds that 5 of them are relevant. 91 Graph of Precision with Ranking: P(r) as we retrieve the 8 documents.Relevant? Y N Y Y N Y N Y Precision P(r) 1 1/ / / / / / / /8 Rank r 92 What does the user want? Restaurant caseThe user wants to find a restaurant serving Sashimi. User uses 2 IR systems. How we can say which one is better? 93 Human judgments are Expensive InconsistentBetween raters Over time Decay in value as documents/query mix evolves Not always representative of “real users” Rating vis-à-vis query, vs underlying need So – what alternatives do we have? 94 Using user Clicks 95 What do clicks tell us? # of clicks received Strong position bias, so absolute click rates unreliable 96 Relative vs absolute ratingsUser’s click sequence Hard to conclude Result1 > Result3 Probably can conclude Result3 > Result2 97 Pairwise relative ratingsPairs of the form: DocA better than DocB for a query Doesn’t mean that DocA relevant to query Now, rather than assess a rank-ordering wrt per-doc relevance assessments Assess in terms of conformance with historical pairwise preferences recorded from user clicks BUT! Don’t learn and test on the same ranking algorithm I.e., if you learn historical clicks from nozama and compare Sergey vs nozama on this history … 98 Comparing two rankings via clicks (Joachims 2002)Query: [support vector machines] Ranking A Ranking B Kernel machines Kernel machines SVM-light SVMs Lucent SVM demo Intro to SVMs Royal Holl. SVM Archives of SVM SVM software SVM-light SVM tutorial SVM software 99 Interleave the two rankingsKernel machines Kernel machines SVMs This interleaving starts with B SVM-light Intro to SVMs Lucent SVM demo Archives of SVM Royal Holl. SVM SVM-light … 100 Remove duplicate resultsKernel machines Kernel machines SVMs SVM-light Intro to SVMs Lucent SVM demo Archives of SVM Royal Holl. SVM SVM-light … 101 Count user clicks A, B Clicks Ranking A: 3 Ranking B: 1 A A …Kernel machines A, B Kernel machines Clicks SVMs Ranking A: 3 Ranking B: 1 SVM-light A Intro to SVMs Lucent SVM demo A Archives of SVM Royal Holl. SVM SVM-light … 102 Interleaved ranking Present interleaved ranking to usersStart randomly with ranking A or ranking B to evens out presentation bias Count clicks on results from A versus results from B Better ranking will (on average) get more clicks 103 A/B testing at web search enginesSec A/B testing at web search engines Purpose: Test a single innovation Prerequisite: You have a large search engine up and running. Have most users use old system Divert a small proportion of traffic (e.g., 1%) to an experiment to evaluate an innovation Interleaved experiment Full page experiment 104 Facts/entities (what happens to clicks?) 105 Recap 106 For ad hoc IR evaluation, need:A document collection A test suite of information needs, expressible as queries A set of relevance judgments, standardly a binary. Download Dolit HttpFtp kernel demo latest version for Windows free to try. Dolit HttpFtp kernel demo latest update: Aug Download Dolit HttpFtp kernel demo latest version for Windows free to try. Dolit HttpFtp kernel demo latest update: Aug.Dolit HttpFtp kernel demo for Windows - Free download and
Property to Gaussian and Kernel estimators for MI and conditional MI, including with surrogates (only option for kernel);Enabled use of different bases for different variables in MI discrete estimator;All new above features enabled in AutoAnalyser;Added drop-down menus for parameters in AutoAnalyser;Included long-form lecture slides in course folder;26/11/2017 - New jar and full distribution files available for release v1.4; Changes for v1.4 include:Major expansion of functionality for AutoAnalysers: adding Launcher applet and capability to double click jar to launch, added Entropy, CMI, CTE and AIS AutoAnalysers, also added binned estimator type, added all variables/pairs analysis, added statistical significance analysis, and ensured functionality of generated Python code with Python3;Added GPU (cuda) capability for KSG Mutual Information calculator (proper documentation and wiki page to come), including unit tests;Added fast neighbour search implementations for mixed discrete-continuous KSG MI estimators;Expanded Gaussian estimator for multi-information (integration);Made all demo/data files readable by Matlab.17/12/2016 - New book out from J. Lizier et al., "An Introduction to Transfer Entropy: Information Flow in Complex Systems" published by Springer, which contains various examples using JIDT (distributed in our releases)21/10/2016 - New jar and full distribution files available for release v1.3.1; Changes for v1.3.1 include:Major update to TransferEntropyCalculatorDiscrete so as to implement arbitrary source and dest embeddings and source-dest delay;Conditional TE calculators (continuous) handle empty conditional variables;Added new auto-embedding method for AIS and TE which maximises bias corrected AIS;Added getNumSeparateObservations() method to TE calculators to make reconstructing/separating local values easier after multiple addObservations() calls;Fixed kernel estimator classes to return proper densities, not probabilities;Bug fix in mixed discrete-continuous MI (Kraskov) implementation;Added simple interface for adding joint observations for MultiInfoCalculatorDiscreteIncluding compiled class files for the AutoAnalyser demo in distribution;Updated Python demo 1 to show use of numpy arrays with ints;Added Python demo 7 and 9 for TE Kraskov with ensemble method and auto-embedding respectively;Added Matlab/Octave example 10 for conditional TE via Kraskov (KSG) algorithm;Added utilities to prepare for enhancing surrogate calculations with fast nearest neighbour search;Minor bug patch to Python readFloatsFile utility.19/7/2015 - New jar and full distribution files available for release v1.3; Changes for v1.3 include:Added AutoAnalyser (Code Generator) GUI demo for MI and TE;Added auto-embedding capability via Ragwitz criteria for AIS and TE calculators (KSG estimators);Added Java demo 9 for showcasing use of Ragwitz auto-embedding;Adding small amount of noise to data in all KSG estimators now by default (may be disabled via setProperty());Added getProperty() methods for all conditional MI and TE calculators;Upgraded Python demos for Python 3 compatibility;Fixed bias correction on mixed discrete-continuous KSG calculators;Updated the tutorial slides to those in use for ECAL 2015 JIDT tutorial.12/2/2015 - New jar and full distribution files available for release v1.2.1; Changes for v1.2.1 include:Added tutorial slides, description of exercises and sample exercise solutions;Made jar target Java 1.6;Added Schreiber TE heart-breath rate with KSG estimator demo code for Python.28/1/2015 - New jar and full distribution files available for release v1.2; Changes for v1.2 include:Dynamic correlation exclusion, or Theiler window, added to all Kraskov estimators;Added univariate MI calculation to simple demo 6;Added Java code for Schreiber Compromise your system. While the hardware mechanisms used by PACMAN cannot be patched with software features, memory corruption bugs can be.Can I tell if someone is using PACMAN against me?Much like the Spectre attack our work is based on, PACMAN executes entirely in the speculative regime and leaves no logs. So, “probably not.”Why are you loading a kext?You may be wondering why our attack begins by loading a custom kernel extension (kext). This kext does two things: 1) adds an artificial software bug to the kernel for us to attack, and 2) adds a PACMAN Gadget.Neither of those things requires a kext- an attacker can find both in the vanilla kernel.An attacker with a software bug doesn’t need a kext.Why do you need a software bug to do the PACMAN attack?PACMAN takes an existing software bug (memory read/ write) and turns it into a more powerful primitive (pointer authentication bypass). For our demo, we add our own bug to the kernel using a kext.In a real world attack, you would just find an existing kernel bug.Our demo only uses the kext for adding a software bug. The entire attack runs in userspace. So, an attacker with an existing bug could do the same attack without the kext.Is PACMAN being used in the wild?To our knowledge, no.Does PACMAN have a logo?Yeah!Does Apple know?We reported our findings and proof-of-concept code to Apple, and have been in talks with them since 2021.How does PACMAN work?PACMAN takes an existing software bug (memory read/ write) and turns it into a more serious exploitation primitive (a pointer authentication bypass), which may lead to arbitrary code execution.In order to do this, we need to learn what the PAC value is for a particular victim pointer.PACMAN does this by creating what we call a PAC Oracle, which is the ability to tell if a given PAC matches a specified pointer. The PAC Oracle must never crash if an incorrect guess is supplied. We then brute force all possible PAC values using the PAC Oracle.A hardware/ software co-attack.We suppress crashes by performing each PAC guess speculatively to prevent anyDolit HttpFtp kernel demo para Windows - CNET Download
Infrastructure for outstanding performance-per-dollarInnovative chiplet processor design that maximizes efficiencyCPU TDPs as low as 65W to help reduce power usage, support sustainability efforts, and optimize rack utilization Virtuozzo Hybrid Server with AMD Processors Virtuozzo powers high density, high performance VPS hosting for companies all over the world. By running Virtuozzo on AMD server processors, hosts can ensure they get the best density and performance possible. Efficient memory management and truly elastic RAMSignificant memory deduplication and disk IOPS/IO savingLess overhead for disk I/O operations and network operationsRebootless kernel updatesHigh Availability for VMs and containersIntegrated storage and backupsSelf-service portals for admins and usersCost-efficient Lite edition also availableValidated with AMD EPYC™ and AMD Ryzen™ CPUs Self-service portal and Infrastructure admin panel Host OS Kernel with virtualization layer Host OS Kernel with virtualization layer Validated AMD Ryzen™-based server system Server Model: 1U4LW-X570/2L2T Validation details: Server Validation Report Ask for your free trial server and license Try Before You Buy Get a Virtuozzo Hybrid Server license and an AMD Ryzen™ Demo System free of charge for up to 1 month. Contact Virtuozzo to get started!Dolit HttpFtp kernel demo para Windows - Descargas gratis y
Shareware Size: 1.3 MB Download Counter: 132 Released: January 08, 2010 | Added: February 05, 2010 | Viewed: 2234 URGENTRECOVERY Professional 3.2 URGENTRECOVERY for Windows is a safe and affordable do-it-yourself data recovery solution that is designed to recover lost and deleted files from all types of media such as hard drives, floppy drives, SmartMedia, CompactFlash, Memory Sticks, and other types of removable media. URGENTRECOVERY... DOWNLOAD GET FULL VER Cost: $114.46 USD, 92.99 EUR License: Demo Size: 5.6 MB Download Counter: 7 Released: June 15, 2005 | Added: June 18, 2005 | Viewed: 919 R-Linux 1.0 R-Linux is a data recovery and undelete utility for Ext2FS (Linux) file system. File recovery after power failure, system crash, virus infection or partition reformation, even for the different file system. Unformat and unerase tool. Creation of image files an entire disk, partition or its part.... DOWNLOAD Cost: $0.00 USD License: Freeware Size: 1.3 MB Download Counter: 42 Released: August 25, 2003 | Added: August 28, 2003 | Viewed: 3009 Kernel Linux - Data Recovery Software 4.0.2 Kernel for Linux data recovery software recovers the damaged data and files from your Linux hard drive. This software recovers the deleted partitions and damaged super blocks, inode tables, group descriptor blocks. The drives supported by the software are; IDE, SCSI, EIDE, SATA, PAN, USB and... DOWNLOAD GET FULL VER Cost: $49.00 USD, 2160.00 INR License: Demo Size: 2.3 MB Download Counter: 21 Released: December 18, 2006 | Added: December 21, 2006 | Viewed: 1621 Pen Drive. Download Dolit HttpFtp kernel demo latest version for Windows free to try. Dolit HttpFtp kernel demo latest update: Aug Download Dolit HttpFtp kernel demo latest version for Windows free to try. Dolit HttpFtp kernel demo latest update: Aug.Dolit software-dolit PDF products
Lotus Notes 8.0, 7.0, 6.5 for pst to nsf conversion installed on Windows 98/2000/2003/XP/Vista operating systems. Free to try demo version of Kernel for PST to NSF lets you experience the pst to nsf conversion where it only saves first 10 emails per folder existing in the PST file. Note: Download That periodically updates software info, pricing of Kernel for PST to NSF from the developer. Please confirm all information before relying on it. Software piracy is theft and impact the entire global economy.Distribution of Kernel for PST to NSF cracked software is generally an illegal act of copyright infringement. Using crack, password, serial numbers, registration codes, key generators is illegal. We donot support crack software licensing and distribute these releases of Kernel for PST to NSF. Kernel For Lotus Notes To Outlook CrackedTop Downloads of Utilities / File Tools: Management TooolsTitle / Version / DescriptionSizeLicenseNucleus Kernel Excel File Recovery 7.05.01 - Nucleus Kernel Excel is a advance easy to use excel file repair software for restoring contents...2.5 MBSharewareRecoveryFix for Outlook PST Repair 4.05.01 - RecoveryFix for Outlook PST repair Software, repair the damaged outlook pst file. Software also...1.6 MBSharewareUndelete SD card 2.3 - Undelete SD card is a photo recovery tool for helping you to recover all types of accidentally...2.3 MBSharewareDisk Doctors NTFS Data Recovery 1.0.1 - Disk Doctors NTFS Data Recovery software supports missing or lost partition recovery, deleted...3.2 MBSharewareFile / Folder Clean-Up Tool(Path too long) 1.1 - Windows tool to delete files and folders with long and corrupted paths. Just browse to the file...172.9 KBDemoAuslogics Disk Defrag 3.4.3 - Disk Defrag will speed up your computer by optimizing file system. It can defragment files,...4.9 MBFreewareEasy Duplicate Finder 1.3 - Easy Duplicate File Finder is a free powerful tool, that helps you to find and delete duplicate...650.1 KBFreewareConvert NSF to PST 8.06.01 - Best nsf to pst converter software to migrate from Lotus Domino environment to MS Exchange...3.4 MBSharewareDBX Repair 9.04.01 - Get competent Outlook Express DBX recovery with advanced Kernel for Outlook Express which...3.1 MBSharewareWinMount 3.5.0913 - WinMount is a compression tool, also a virtual disk tool ( Mount RAR ZIP MOU and CD DVD HDD...3.5 MBSharewareComments
The driver, runPTEditorLoader.exe --unloadAlternatively, you can also use any other driver-loading tool, e.g., OSRLoader or NoVirusThanks Kernel-Mode Driver Loader.Install Kernel Part From SourceLinuxBuilding the kernel module requires the kernel headers of the kernel. On Ubuntu, they can be installed by runningsudo apt install linux-headers-$(uname -r)Both the library and the the kernel module can be build by runningThe resulting kernel module can be loaded usingsudo insmod module/pteditor.koWindowsThe kernel driver for Windows requires Visual Studio with Visual C++, the Windows SDK, and the Windows Driver Kit (WDK) to build.Using the Visual Studio project, the driver can then simply be built from Visual Studio.RequirementsThe library requires a recent Linux kernel (continuously tested on the current kernel for Ubuntu 16.04 (kernel 4.15), 18.04 (kernel 5.3), and 20.04 (kernel 5.8)) or Windows 10.It supports both x86_64 and ARMv8.The library does not rely on any other library. It uses only standard C functionality.On Linux, the library does not require root privileges, whereas on Windows it requires administrator privileges.TestTo test whether the kernel part and the library works, the repository contains unit tests.The tests are found in the folder test and can be compiled with make (Linux) or Visual Studio (Windows).ExampleThe basic functionality (ptedit_init and ptedit_cleanup) is always required.After the initialization, all functions provided by the library can be used.For examples see example.c or the examples in the demo folder.The demo folder contains multiple examples:memmap: Starting from the root of paging, the demo iterates through all page tables of all levels and dumps the contents of the entries.map_pt: A Rowhamer exploit simulation, which maps the page table to a user-accessible address for manipulation.uncachable: This demos manipulates the memory type of a mapping to uncachable and back to cachable.nx: After setting a function to non-executable, it uses the page tables to make the function executable again.virt2phys: Converts a
2025-04-04Nucleus Data Recovery Kernel for Word Recovery recovers corrupted word document files corrupted due to unexpected system shutdown, virus attacks or error reading media where word document are stored. The software uses Live Preview technology. After complete scanning the corrupted or damaged word document which are recoverable are shown in the preview window, then recovered data is copied at the user defined location. Multiple doc files are repaired in a single repair cycle. Kernel for Word Document Repair Software uses quick algorithm for searching and repairing the corruptions in the corrupted document files and hence is a fast, simple and easy to use Word Document Repair Software, which helps you to recover and repair your corrupt document files in minutes. Kernel for Word recovery software’s supported versions includes MS Word 2010, 2007, 2003, 2000, 97, 95 and 6.0 documents. Free demo version of the software is available for easy download. Demo version recovers and saves recovered data to new Word file at the defined location. However, the file repaired using demo version will have stamp Demo after every paragraph. User Rating: 1.5 (2 votes) Currently 1.50/512345 OS: Win2000, Windows 7 x32, Windows 7 x64, WinServer, Windows Vista, Windows Vista x64, Windows XP Requirements: Pentium II 400 MHz, 64 MB RAM, 10 MB
2025-03-28With RankingExample "Your query found 349,871 possibly relevant documents. Here are the first eight." Examination of the first 8 finds that 5 of them are relevant. 91 Graph of Precision with Ranking: P(r) as we retrieve the 8 documents.Relevant? Y N Y Y N Y N Y Precision P(r) 1 1/ / / / / / / /8 Rank r 92 What does the user want? Restaurant caseThe user wants to find a restaurant serving Sashimi. User uses 2 IR systems. How we can say which one is better? 93 Human judgments are Expensive InconsistentBetween raters Over time Decay in value as documents/query mix evolves Not always representative of “real users” Rating vis-à-vis query, vs underlying need So – what alternatives do we have? 94 Using user Clicks 95 What do clicks tell us? # of clicks received Strong position bias, so absolute click rates unreliable 96 Relative vs absolute ratingsUser’s click sequence Hard to conclude Result1 > Result3 Probably can conclude Result3 > Result2 97 Pairwise relative ratingsPairs of the form: DocA better than DocB for a query Doesn’t mean that DocA relevant to query Now, rather than assess a rank-ordering wrt per-doc relevance assessments Assess in terms of conformance with historical pairwise preferences recorded from user clicks BUT! Don’t learn and test on the same ranking algorithm I.e., if you learn historical clicks from nozama and compare Sergey vs nozama on this history … 98 Comparing two rankings via clicks (Joachims 2002)Query: [support vector machines] Ranking A Ranking B Kernel machines Kernel machines SVM-light SVMs Lucent SVM demo Intro to SVMs Royal Holl. SVM Archives of SVM SVM software SVM-light SVM tutorial SVM software 99 Interleave the two rankingsKernel machines Kernel machines SVMs This interleaving starts with B SVM-light Intro to SVMs Lucent SVM demo Archives of SVM Royal Holl. SVM SVM-light … 100 Remove duplicate resultsKernel machines Kernel machines SVMs SVM-light Intro to SVMs Lucent SVM demo Archives of SVM Royal Holl. SVM SVM-light … 101 Count user clicks A, B Clicks Ranking A: 3 Ranking B: 1 A A …Kernel machines A, B Kernel machines Clicks SVMs Ranking A: 3 Ranking B: 1 SVM-light A Intro to SVMs Lucent SVM demo A Archives of SVM Royal Holl. SVM SVM-light … 102 Interleaved ranking Present interleaved ranking to usersStart randomly with ranking A or ranking B to evens out presentation bias Count clicks on results from A versus results from B Better ranking will (on average) get more clicks 103 A/B testing at web search enginesSec A/B testing at web search engines Purpose: Test a single innovation Prerequisite: You have a large search engine up and running. Have most users use old system Divert a small proportion of traffic (e.g., 1%) to an experiment to evaluate an innovation Interleaved experiment Full page experiment 104 Facts/entities (what happens to clicks?) 105 Recap 106 For ad hoc IR evaluation, need:A document collection A test suite of information needs, expressible as queries A set of relevance judgments, standardly a binary
2025-04-16